Hello,
I’m new at OpenDistro ES.
Trying to configure OpenDistro Elasticsearch SAML using these instructions.
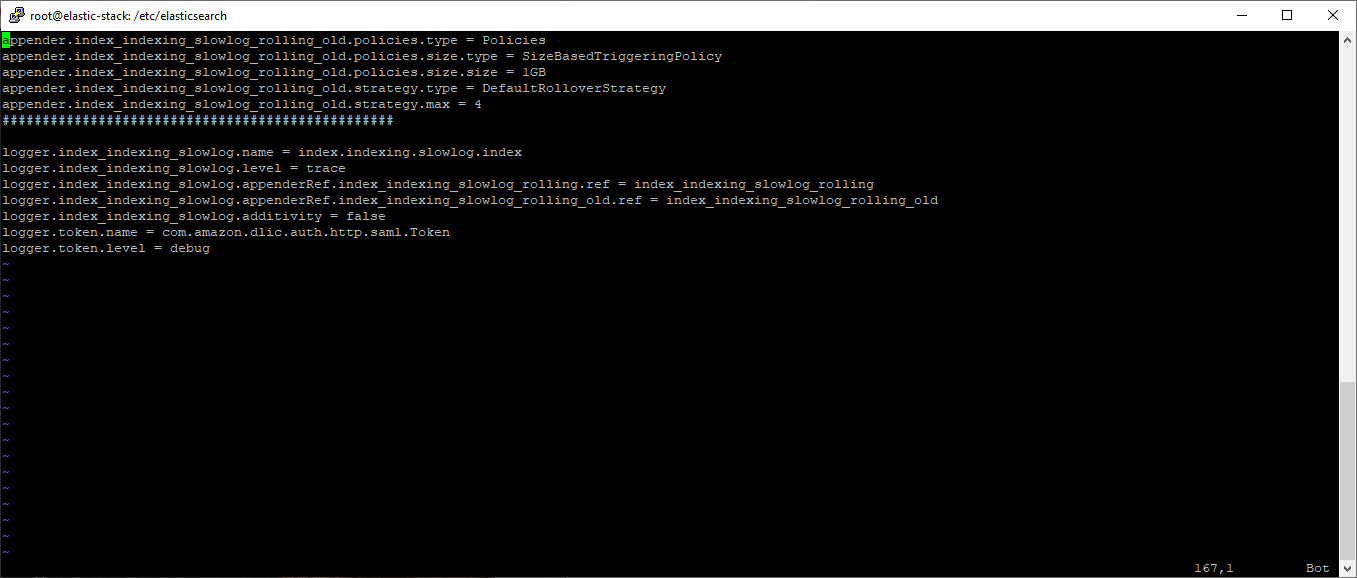
My error in Kibana after the configuration were made is shown below. These were found by executing this command “journalctl -u kibana.service”.
Kibana.Service_logs
Jul 14 21:25:59 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:25:59 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
Jul 14 21:25:59 elastic-stack kibana[50516]: Error: failed parsing SAML config
Jul 14 21:25:59 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:25:59 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
Jul 14 21:25:59 elastic-stack kibana[50516]: Error: failed parsing SAML config
Jul 14 21:25:59 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:25:59 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
Jul 14 21:25:59 elastic-stack kibana[50516]: Error: failed parsing SAML config
Jul 14 21:25:59 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:25:59 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
Jul 14 21:26:00 elastic-stack kibana[50516]: Error: failed parsing SAML config
Jul 14 21:26:00 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:26:00 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
Jul 14 21:26:00 elastic-stack kibana[50516]: Error: failed parsing SAML config
Jul 14 21:26:00 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:26:00 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
Jul 14 21:44:06 elastic-stack kibana[50516]: Error: failed parsing SAML config
Jul 14 21:44:06 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:44:06 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
Jul 14 21:44:06 elastic-stack kibana[50516]: Error: failed parsing SAML config
Jul 14 21:44:06 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:44:06 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
Jul 14 21:44:06 elastic-stack kibana[50516]: Error: failed parsing SAML config
Jul 14 21:44:06 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:44:06 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
Jul 14 21:44:06 elastic-stack kibana[50516]: Error: failed parsing SAML config
Jul 14 21:44:06 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:44:06 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
Jul 14 21:44:06 elastic-stack kibana[50516]: Error: failed parsing SAML config
Jul 14 21:44:06 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:44:06 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
Jul 14 21:44:07 elastic-stack kibana[50516]: Error: failed parsing SAML config
Jul 14 21:44:07 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:44:07 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
Jul 14 21:44:07 elastic-stack kibana[50516]: Error: failed parsing SAML config
Jul 14 21:44:07 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:44:07 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
Jul 14 21:44:07 elastic-stack kibana[50516]: Error: failed parsing SAML config
Jul 14 21:44:07 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:44:07 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
Jul 14 21:44:07 elastic-stack kibana[50516]: Error: failed parsing SAML config
Jul 14 21:44:07 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:44:07 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
Jul 14 21:44:08 elastic-stack kibana[50516]: Error: failed parsing SAML config
Jul 14 21:44:08 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:44:08 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
Jul 14 21:44:08 elastic-stack kibana[50516]: Error: failed parsing SAML config
Jul 14 21:44:08 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:44:08 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
Jul 14 21:44:08 elastic-stack kibana[50516]: Error: failed parsing SAML config
Jul 14 21:44:08 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:44:08 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
Jul 14 21:44:08 elastic-stack kibana[50516]: Error: failed parsing SAML config
Jul 14 21:44:08 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:44:08 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
Jul 14 21:44:08 elastic-stack kibana[50516]: Error: failed parsing SAML config
Jul 14 21:44:08 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:44:08 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
Jul 14 21:44:09 elastic-stack kibana[50516]: Error: failed parsing SAML config
Jul 14 21:44:09 elastic-stack kibana[50516]: at SecurityClient.getSamlHeader (/usr/share/kibana/plugins/opendistroSecurityKibana/server/backend/opendistro_security_client.ts:176:15)
Jul 14 21:44:09 elastic-stack kibana[50516]: at process._tickCallback (internal/process/next_tick.js:68:7)
I looked through these posts below , but some were never answered, or it wasn’t related to my environment issue.
https://forum.opensearch.org/search?q=SAML
My Environment:
Using Open Distro for Elasticsearch 1.13.2
Elasticsearch.yml
root@elastic-stack:/etc/elasticsearch# grep -v "^#\|^$" elasticsearch.yml
path.data: /var/lib/elasticsearch
path.logs: /var/log/elasticsearch
network.host: 10.200.6.21
http.port: 9200
discovery.type: single-node
action.auto_create_index: true
opendistro_security.ssl.transport.pemcert_filepath: /etc/elasticsearch/admin.pem
opendistro_security.ssl.transport.pemkey_filepath: /etc/elasticsearch/admin-key.pem
opendistro_security.ssl.transport.pemtrustedcas_filepath: /etc/elasticsearch/root-ca.pem
opendistro_security.ssl.transport.enforce_hostname_verification: false
opendistro_security.ssl.http.enabled: true
opendistro_security.ssl.http.pemcert_filepath: /etc/elasticsearch/admin.pem
opendistro_security.ssl.http.pemkey_filepath: /etc/elasticsearch/admin-key.pem
opendistro_security.ssl.http.pemtrustedcas_filepath: /etc/elasticsearch/root-ca.pem
opendistro_security.allow_unsafe_democertificates: false
opendistro_security.allow_default_init_securityindex: true
opendistro_security.authcz.admin_dn:
- 'CN=elastic-stack.enseva-labs.net,OU=admin,O=enseva,L=cedar rapids,ST=iowa,C=us'
opendistro_security.audit.type: internal_elasticsearch
opendistro_security.enable_snapshot_restore_privilege: true
opendistro_security.check_snapshot_restore_write_privileges: true
opendistro_security.restapi.roles_enabled: ["all_access", "security_rest_api_access"]
opendistro_security.system_indices.enabled: true
opendistro_security.system_indices.indices: [".opendistro-alerting-config", ".opendistro-alerting-alert*", ".opendistro-anomaly-results*", ".opendistro-anomaly-detector*", ".opendistro-anomaly-checkpoints", ".opendistro-anomaly-detection-state", ".opendistro-reports-*", ".opendistro-notifications-*", ".opendistro-notebooks", ".opendistro-asynchronous-search-response*"]
cluster.routing.allocation.disk.threshold_enabled: false
node.max_local_storage_nodes: 3
Kibana.yml
root@elastic-stack:/etc/kibana# grep -v "^#\|^$" kibana.yml
server.host: "10.200.6.21"
server.port: 5601
server.name: "elastic-stack.enseva-labs.net"
server.ssl.enabled: true
server.ssl.key: "/etc/kibana/admin-key.pem"
server.ssl.certificate: "/etc/kibana/admin.pem"
elasticsearch.hosts: "https://elastic-stack.enseva-labs.net:9200"
elasticsearch.username: admin
elasticsearch.password: admin
elasticsearch.requestHeadersWhitelist: ["securitytenant","Authorization"]
elasticsearch.ssl.certificateAuthorities: "/etc/kibana/root-ca.pem"
elasticsearch.ssl.verificationMode: none
opendistro_security.multitenancy.enabled: true
opendistro_security.multitenancy.tenants.preferred: ["Private", "Global"]
opendistro_security.readonly_mode.roles: ["kibana_read_only"]
opendistro_security.auth.type: "saml"
server.xsrf.whitelist: ["/_opendistro/_security/saml/acs", "/_opendistro/_security/saml/logout"]
opendistro_security.cookie.secure: false
newsfeed.enabled: false
telemetry.optIn: false
telemetry.enabled: false
security.showInsecureClusterWarning: false
map.includeElasticMapsService: false
logging.dest: '/etc/kibana/kibana.log'
opendistro_security/securityconfig/config.yml
---
_meta:
type: "config"
config_version: 2
config:
dynamic:
# Set filtered_alias_mode to 'disallow' to forbid more than 2 filtered aliases per index
# Set filtered_alias_mode to 'warn' to allow more than 2 filtered aliases per index but warns about it (default)
# Set filtered_alias_mode to 'nowarn' to allow more than 2 filtered aliases per index silently
#filtered_alias_mode: warn
#do_not_fail_on_forbidden: false
#kibana:
# Kibana multitenancy
#multitenancy_enabled: true
#server_username: kibanaserver
#index: '.kibana'
http:
anonymous_auth_enabled: false
xff:
enabled: false
internalProxies: '192\.168\.0\.10|192\.168\.0\.11' # regex pattern
#internalProxies: '.*' # trust all internal proxies, regex pattern
#remoteIpHeader: 'x-forwarded-for'
###### see https://docs.oracle.com/javase/7/docs/api/java/util/regex/Pattern.html for regex help
###### more information about XFF https://en.wikipedia.org/wiki/X-Forwarded-For
###### and here https://tools.ietf.org/html/rfc7239
###### and https://tomcat.apache.org/tomcat-8.0-doc/config/valve.html#Remote_IP_Valve
authc:
kerberos_auth_domain:
http_enabled: false
transport_enabled: false
order: 6
http_authenticator:
type: kerberos
challenge: true
config:
# If true a lot of kerberos/security related debugging output will be logged to standard out
krb_debug: false
# If true then the realm will be stripped from the user name
strip_realm_from_principal: true
authentication_backend:
type: noop
basic_internal_auth_domain:
description: "Authenticate via HTTP Basic against internal users database"
http_enabled: true
transport_enabled: true
order: 0
http_authenticator:
type: basic
challenge: true
authentication_backend:
type: intern
proxy_auth_domain:
description: "Authenticate via proxy"
http_enabled: false
transport_enabled: false
order: 3
http_authenticator:
type: proxy
challenge: false
config:
user_header: "x-proxy-user"
roles_header: "x-proxy-roles"
authentication_backend:
type: noop
jwt_auth_domain:
description: "Authenticate via Json Web Token"
http_enabled: false
transport_enabled: false
order: 0
http_authenticator:
type: jwt
challenge: false
config:
signing_key: "base64 encoded HMAC key or public RSA/ECDSA pem key"
jwt_header: "Authorization"
jwt_url_parameter: null
roles_key: null
subject_key: null
authentication_backend:
type: noop
clientcert_auth_domain:
description: "Authenticate via SSL client certificates"
http_enabled: false
transport_enabled: false
order: 2
http_authenticator:
type: clientcert
config:
username_attribute: cn #optional, if omitted DN becomes username
challenge: false
authentication_backend:
type: noop
ldap:
description: "Authenticate via LDAP or Active Directory"
http_enabled: false
transport_enabled: false
order: 5
http_authenticator:
type: basic
challenge: false
authentication_backend:
# LDAP authentication backend (authenticate users against a LDAP or Active Directory)
type: ldap
config:
# enable ldaps
enable_ssl: false
# enable start tls, enable_ssl should be false
enable_start_tls: false
# send client certificate
enable_ssl_client_auth: false
# verify ldap hostname
verify_hostnames: true
hosts:
- localhost:8389
bind_dn: null
password: null
userbase: 'ou=people,dc=example,dc=com'
# Filter to search for users (currently in the whole subtree beneath userbase)
# {0} is substituted with the username
usersearch: '(sAMAccountName={0})'
# Use this attribute from the user as username (if not set then DN is used)
username_attribute: null
saml_auth_domain:
order: 1
description: "SAML provider"
http_enabled: true
transport_enabled: false
http_authenticator:
type: saml
challenge: true
config:
idp:
metadata_file: /usr/share/elasticsearch/plugins/opendistro_security/securityconfig/keycloak.xml
entity_id: http://keycloak.enseva-labs.net:8080/auth/realms/elastic/
sp:
entity_id: elastic
forceAuthn: true
kibana_url: https://elastic-stack.enseva-labs.net:5601/
roles_key: Role
exchange_key: 76caaaac-77d8-450a-803d-87364e8a5203
authentication_backend:
type: noop
authz:
roles_from_myldap:
description: "Authorize via LDAP or Active Directory"
http_enabled: false
transport_enabled: false
authorization_backend:
# LDAP authorization backend (gather roles from a LDAP or Active Directory, you have to configure the above LDAP authentication backend settings too)
type: ldap
config:
# enable ldaps
enable_ssl: false
# enable start tls, enable_ssl should be false
enable_start_tls: false
# send client certificate
enable_ssl_client_auth: false
# verify ldap hostname
verify_hostnames: true
hosts:
- localhost:8389
bind_dn: null
password: null
rolebase: 'ou=groups,dc=example,dc=com'
# Filter to search for roles (currently in the whole subtree beneath rolebase)
# {0} is substituted with the DN of the user
# {1} is substituted with the username
# {2} is substituted with an attribute value from user's directory entry, of the authenticated user. Use userroleattribute to specify the name of the attribute
rolesearch: '(member={0})'
# Specify the name of the attribute which value should be substituted with {2} above
userroleattribute: null
# Roles as an attribute of the user entry
userrolename: disabled
#userrolename: memberOf
# The attribute in a role entry containing the name of that role, Default is "name".
# Can also be "dn" to use the full DN as rolename.
rolename: cn
# Resolve nested roles transitive (roles which are members of other roles and so on ...)
resolve_nested_roles: true
userbase: 'ou=people,dc=example,dc=com'
# Filter to search for users (currently in the whole subtree beneath userbase)
# {0} is substituted with the username
usersearch: '(uid={0})'
# Skip users matching a user name, a wildcard or a regex pattern
#skip_users:
# - 'cn=Michael Jackson,ou*people,o=TEST'
# - '/\S*/'
roles_from_another_ldap:
description: "Authorize via another Active Directory"
http_enabled: false
transport_enabled: false
authorization_backend:
type: ldap
#config goes here ...
# auth_failure_listeners:
# ip_rate_limiting:
# type: ip
# allowed_tries: 10
# time_window_seconds: 3600
# block_expiry_seconds: 600
# max_blocked_clients: 100000
# max_tracked_clients: 100000
# internal_authentication_backend_limiting:
# type: username
# authentication_backend: intern
# allowed_tries: 10
# time_window_seconds: 3600
# block_expiry_seconds: 600
# max_blocked_clients: 100000
# max_tracked_clients: 100000
I used these instructions to install OpenDistro Elasticsearch environment.
Everything is running well, and the setup was easy to install.
I also configured self-signed certificates from these instructions below. That also worked great in my environment.
Once all the configurations are completed I restarted Kibana service (systemctl restart kinbana).
Chrome Browser shows this.
{"statusCode":500,"error":"Internal Server Error","message":"Internal Error"}
I did not notice any Warnings or Errors in my Elasticsearch log file that would pertain to this issue.
In my kibana.log file I did see these error’s
kibana.logs
{"type":"response","@timestamp":"2021-07-15T02:44:09Z","tags":[],"pid":50516,"method":"get","statusCode":401,"req":{"url":"/favicon.ico","method":"get","headers":{"host":"elastic-stack.enseva-labs.net:5601","connection":"keep-alive","pragma":"no-cache","cache-control":"no-cache","sec-ch-ua":"\" Not;A Brand\";v=\"99\", \"Google Chrome\";v=\"91\", \"Chromium\";v=\"91\"","sec-ch-ua-mobile":"?0","user-agent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.124 Safari/537.36","accept":"image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8","sec-fetch-site":"same-origin","sec-fetch-mode":"no-cors","sec-fetch-dest":"image","referer":"https://elastic-stack.enseva-labs.net:5601/auth/saml/login?nextUrl=%2Fapp%2Fopendistro_security","accept-encoding":"gzip, deflate, br","accept-language":"en-US,en;q=0.9"},"remoteAddress":"10.200.6.67","userAgent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.124 Safari/537.36","referer":"https://elastic-stack.enseva-labs.net:5601/auth/saml/login?nextUrl=%2Fapp%2Fopendistro_security"},"res":{"statusCode":401,"responseTime":1,"contentLength":9},"message":"GET /favicon.ico 401 1ms - 9.0B"}
{"type":"error","@timestamp":"2021-07-15T02:55:45Z","tags":["connection","client","error"],"pid":50516,"level":"error","error":{"message":"140710813779776:error:14094416:SSL routines:ssl3_read_bytes:sslv3 alert certificate unknown:../deps/openssl/openssl/ssl/record/rec_layer_s3.c:1544:SSL alert number 46\n","name":"Error","stack":"Error: 140710813779776:error:14094416:SSL routines:ssl3_read_bytes:sslv3 alert certificate unknown:../deps/openssl/openssl/ssl/record/rec_layer_s3.c:1544:SSL alert number 46\n"},"message":"140710813779776:error:14094416:SSL routines:ssl3_read_bytes:sslv3 alert certificate unknown:../deps/openssl/openssl/ssl/record/rec_layer_s3.c:1544:SSL alert number 46\n"}
{"type":"log","@timestamp":"2021-07-15T02:55:45Z","tags":["error","plugins","opendistroSecurityKibana"],"pid":50516,"message":"Failed to get saml header: Error: Error: failed parsing SAML config"}
{"type":"error","@timestamp":"2021-07-15T02:55:45Z","tags":[],"pid":50516,"level":"error","error":{"message":"Internal Server Error","name":"Error","stack":"Error: Internal Server Error\n at HapiResponseAdapter.toError (/usr/share/kibana/src/core/server/http/router/response_adapter.js:132:19)\n at HapiResponseAdapter.toHapiResponse (/usr/share/kibana/src/core/server/http/router/response_adapter.js:86:19)\n at HapiResponseAdapter.handle (/usr/share/kibana/src/core/server/http/router/response_adapter.js:81:17)\n at Router.handle (/usr/share/kibana/src/core/server/http/router/router.js:164:34)\n at process._tickCallback (internal/process/next_tick.js:68:7)"},"url":{"protocol":null,"slashes":null,"auth":null,"host":null,"port":null,"hostname":null,"hash":null,"search":"?nextUrl=%2Fapp%2Fopendistro_security","query":{"nextUrl":"/app/opendistro_security"},"pathname":"/auth/saml/login","path":"/auth/saml/login?nextUrl=%2Fapp%2Fopendistro_security","href":"/auth/saml/login?nextUrl=%2Fapp%2Fopendistro_security"},"message":"Internal Server Error"}
{"type":"response","@timestamp":"2021-07-15T02:55:45Z","tags":[],"pid":50516,"method":"get","statusCode":500,"req":{"url":"/auth/saml/login?nextUrl=%2Fapp%2Fopendistro_security","method":"get","headers":{"host":"elastic-stack.enseva-labs.net:5601","connection":"keep-alive","cache-control":"max-age=0","sec-ch-ua":"\" Not;A Brand\";v=\"99\", \"Google Chrome\";v=\"91\", \"Chromium\";v=\"91\"","sec-ch-ua-mobile":"?0","upgrade-insecure-requests":"1","user-agent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.124 Safari/537.36","accept":"text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9","sec-fetch-site":"cross-site","sec-fetch-mode":"navigate","sec-fetch-user":"?1","sec-fetch-dest":"document","referer":"https://elastic-stack.enseva-labs.net:5601/auth/saml/login?nextUrl=%2Fapp%2Fopendistro_security","accept-encoding":"gzip, deflate, br","accept-language":"en-US,en;q=0.9"},"remoteAddress":"10.200.6.67","userAgent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.124 Safari/537.36","referer":"https://elastic-stack.enseva-labs.net:5601/auth/saml/login?nextUrl=%2Fapp%2Fopendistro_security"},"res":{"statusCode":500,"responseTime":15,"contentLength":9},"message":"GET /auth/saml/login?nextUrl=%2Fapp%2Fopendistro_security 500 15ms - 9.0B"}
{"type":"response","@timestamp":"2021-07-15T02:55:45Z","tags":[],"pid":50516,"method":"get","statusCode":401,"req":{"url":"/favicon.ico","method":"get","headers":{"host":"elastic-stack.enseva-labs.net:5601","connection":"keep-alive","pragma":"no-cache","cache-control":"no-cache","sec-ch-ua":"\" Not;A Brand\";v=\"99\", \"Google Chrome\";v=\"91\", \"Chromium\";v=\"91\"","sec-ch-ua-mobile":"?0","user-agent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.124 Safari/537.36","accept":"image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8","sec-fetch-site":"same-origin","sec-fetch-mode":"no-cors","sec-fetch-dest":"image","referer":"https://elastic-stack.enseva-labs.net:5601/auth/saml/login?nextUrl=%2Fapp%2Fopendistro_security","accept-encoding":"gzip, deflate, br","accept-language":"en-US,en;q=0.9"},"remoteAddress":"10.200.6.67","userAgent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.124 Safari/537.36","referer":"https://elastic-stack.enseva-labs.net:5601/auth/saml/login?nextUrl=%2Fapp%2Fopendistro_security"},"res":{"statusCode":401,"responseTime":3,"contentLength":9},"message":"GET /favicon.ico 401 3ms - 9.0B"}
To sum it up
I installed elasticsearch and Kibana from OpenDistro Documentation along with creating my self-signed certificates. Once that was completed, I sent Logs to my server to make sure it was functioning. No problems were found, and the instruction worked great.
Then I proceeded to configure the server to use SAML by following the instruction that’s when problems occurred.
Problems occured when I uncommented this line in Kibana.yml.
opendistro_security.auth.type: saml
At first, I didn’t notice any errors until I reloaded my browser then they were shown as I stated above.
Any Advice or direction to solve this would be appreciated.
Thank you in advance.